Loading…
How To Prevent Account Hacking | All You Need To Know
Account hacking is on the rise. There are at least 30 billion devices connected online, with each device having access to multiple accounts (mine mobile has over 40 different apps/accounts alone). That is many accounts for cyber criminals to hack.
Hackers aim to access your personal information with a view to either holding it to ransom, or committing crimes such as identity theft. When you think about all our activity online, from banking to social media, there are many opportunities for hackers to cause lots of damage out there.
Cyber criminals use various techniques to access your information, including phishing for access through realistic looking fake e-mails that have Trojan's and other forms of malware that do the damage when the fake link is clicked or attachment opened.
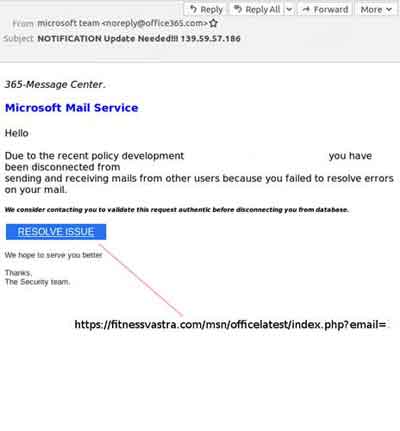 Account Hacking
Account HackingPhishing E-Mail Example
Source:- virusbulletin.com
Once the link is clicked or attachment opened, a series of events are set in motion, which can include keystroke software being installed to pick up all of your actions that enable access to your accounts.
In addition, it is reported that over 60% of people use the same password for all of their accounts. Whilst this is convenient for you, it is also convenient for the cyber criminal. Not keeping up with software patching also presents another attack vector for hackers.
In this article, we simply review good practices you can use to protect your online accounts.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the ultimate BIOS update pack
- Includes a set of checklists and flowcharts to support your BIOS update process
- Also includes the full set of common FAQs from users who experience BIOS update issues
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.
Your Ultimate Account Hacking Prevention Reference Guide
Many resources are online and in book form that offer advice and guidance for protecting yourself whilst connected to the Internet.
One such author is Marc Goodman, who wrote a book called Future Crimes in 2015. It's an excellent source of information, with many prophecies proving to be true. His UPDATE advice to protecting yourself online touches on several themes throughout this section of eComputerZ.
- Update — Patch devices, applications and operating systems frequently;
- Passwords — Use complex and different passwords for all accounts, and MFA;
- Downloads — Only use trusted sites and authorized sources
- Administrator — Don't use admin accounts and give hacks the 'keys to the castle';
- Turn off — Switch off devices and broadband routers when not in use;
- Encryption — Make your data difficult to intercept and unreadable.
Whenever you are interacting with a website, including payments for goods and services, always check for the security padlock next to the website name. This signifies that the site is secure and is encrypting your data as you use the site.
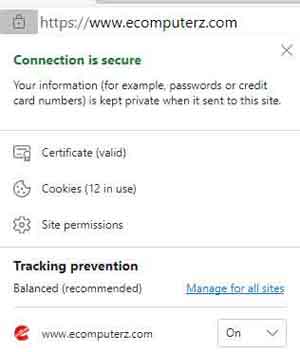 Account Hacking
Account HackingHTTPS Security Padlock Example
It is also worth noting that data hosted on cloud services are unencrypted. Invest in a data encryption tool if possible, so your information is unobtainable if a data breach were to occur.
If you can afford it, subscribe to a good quality VPN service. I am currently subscribed to Mullvad VPN, and apart from some ad-hoc random disconnection issues, the service has been good.
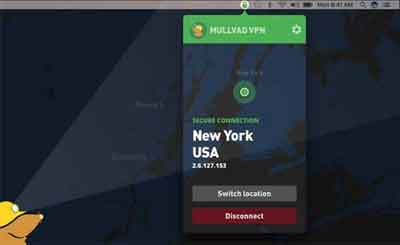 Account Hacking
Account HackingMullvad VPN Service
Source:- macworld.com
It should go without saying that good quality Anti Virus and Anti Malware software packages on all of your devices is a must to protect against account hacking methods and techniques.
However, it is worth noting Anti Virus and Anti Malware solutions are only part of the overall approach, whereas once upon a time, this was more than sufficient
 Account Hacking
Account HackingAnti Virus Statistic
Source:- futurecrimesbook.com
Therefore, to prevent losing your information to a Ransomware attack, for example, make sure you have a robust data backup plan in place. Furthermore, ensure where possible you use your personal devices at home rather than public devices, or public Wi-Fi networks.
If you must use public devices or public Wi-Fi networks, always make sure you log out of any accounts you log in to, and clear down your Internet History.
In addition, turn off sharing so resources such as printers and storage devices that you usually access cannot be discovered if your device is compromised.
In addition, always think twice about the data you submit online and who with. If they have a data breach, it's your information that's at risk of being exploited.
Phishing e-mails are easy to target at regularly accessed e-mail accounts. How many e-mails do you simply delete from your main account? Have you checked how many e-mails are in your spam filter?
Always delete suspicious e-mails without opening them, even if they are from someone you know, or a source you can typically Trust. If they appear 'off', then be sensible and remove as soon as you get the chance. Let the person know their account may be compromised. They'll be very appreciative, and it stops further propagation of the hackers phishing scam.
Also let people know in your contacts list if you are unfortunate to have your account hacked. They will know not to open any correspondence from you until the matter is resolved.
Do not send any sensitive information, such as private medial details or banking information, by e-mail. Information sent out in this way is not secure by encryption methods and are easy pickings for hackers. Don't make their lives easy.
If you are looking to create a new account for something you are uncertain will be used long-term, create a temporary e-mail account with a provider such as Guerrilla Mail that will be auto-deleted after 24 hours.
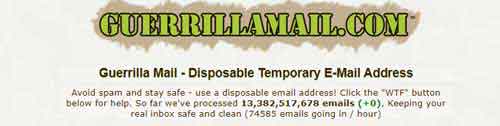 Account Hacking
Account HackingBurner E-Mail Accounts
Social media accounts are often targeted by those perpetuating account hacking. For each account, make sure you review all possible security settings and enable, for example, login alerts, so you know if someone else has accessed your account.
For mobile apps, make sure you understand and set all permissions to suit your security needs.
Consider taking security a step further by understanding the information each app will access, and ultimately share, before installing.
In addition, only download apps from verified sources, such as the Apple App Store.
Whilst we are on the subject of social media, think twice about what you share. Ask yourself if what's on your story that could aid cyber criminals capture and exploit your accounts and data.
Furthermore, don't blindly accept friend requests from people you don't know, or people you do know, but their account behaviour does match with the person you know or love. It could be a fake account, or their account has already been hacked. The same goes for e-mails.
When using mobile devices, ensure you use biometric and pattern lock style PINs where possible. See the Mobile Phone Security Awareness article for more detail. Furthermore, clearly understand how to remotely lock and wipe your device if lost or stolen.
 Account Hacking
Account HackingTrack and Wipe Your Lost or Stolen Mobile Device
In addition to keeping tabs on your mobile devices, another area to monitor is the security status of the websites you regularly use. Perform online searches or use sites such as Vigilante to see their current status.
If you find a website that you log in to has been compromised, make sure you change the password for that site immediately.
In a similar vein, you can check to see if any of your accounts have been compromised. Simply enter your e-mail address in to the 'Have I Been Pawned' site.
Again, if the results show accounts that use your e-mail address have been hacked, close those accounts down that you no longer use, if possible, but continually change the password for each account.
It's difficult to keep on top of all accounts with their different usernames/e-mail addresses and password lengths, complexity and reset durations.
An option is to use a good quality password manager that will securely manage your different login details for you.
I am currently using the McAfee True Key TM product. It seamlessly interacts within your web browser and is capable of creating very long and complex passwords, which are incredibly difficult to crack.
 Account Hacking
Account HackingMcAfee True Key Password Manager
In addition to setting complex passwords, enable multifactor authentication as an added layer of security when it is available.
Modern web browsers and sites have facilities that save your information for future use, including account log in details, common forms fields such as home addresses, and bank card details. Be careful with what information you choose to be saved for convenience.
How To Prevent Account Hacking | Final Thoughts
The only foolproof method to prevent account hacking is to delete all of your online accounts and remove yourself from any online activity.
It is likely this approach is not appropriate for the majority of people these days because it disconnects you from friends, family, and all the conveniences the online world has available.
Therefore, please make the effort to adopt as many of the actions presented in this article as soon as possible. I know it's a pain, and time-consuming, but it is more than worth the effort if it means your online data remains secure.
Finally, to prevent further risk of account hacking, take a note of the following tips and article references for further information on this subject.
- Use a credit card when making online purchases, as credit card companies are more likely to compensate you for your loss if you are subject to fraud than PayPal or your bank
- Change your login and administrator password to your home broadband router. Last thing you need is someone snooping on your home network with easy access to your devices.
- If you don't have a modern laptop that has a webcam privacy cover, make sure you cover your webcam on all devices when not in use with a sicker or black tape. If your device is compromised, the hackers could be watching what you do.
- I enjoyed reading this article on how to protect your Instagram from being hacked. Instagram is incredibly popular and there is every chance you have an account already.
- I also enjoyed this Ask Leo article about preventing your accounts from being hacked.
Was this page helpful?
Thanks! ✅