Loading…
A Software Application Security Patching Plan For Home Users
A software application security patching plan is essential in today's world. Organizations struggle to patch their devices, and have suffered the consequences. I don't want this happening to you.
This article is focused on how you can keep your devices patched to protect against software vulnerabilities that could be exploited and put your personal data at risk.
Articles on this subject tend to be focused on businesses with many devices and different software applications. I don't see many (or any, for that matter) that focuses on home computers users.
Therefore, I've taken the best practices businesses should follow, and adapted them for home users. The six-step plan for home users will, I think, at least generate some ideas for improving the security of your home devices.
This article also looks at the fundamentals of software patching, such as what it is and why it is important. We also look at how to automate software patching using native operating system settings, and 3rd party tools.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the ultimate BIOS update pack
- Includes a set of checklists and flowcharts to support your BIOS update process
- Also includes the full set of common FAQs from users who experience BIOS update issues
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.
What Is System Patching And Why Is It Important?
System patching is usually the process of applying or installing a small software program made available by the software vendor that resolves a specific issue with their software products.
Often this is a fault, or bug, with the software programming. The bug is typically related to a vulnerability that could be exploited by cyber criminals.
The vulnerability could be, for example, a programming routine that is unable to process or handle the programming routines coded in a malicious ransomware attack program.
This could mean that the vulnerability allows the ransomware program to run its programming routines, and therefore infecting that device.
From here the malware can hold the device, or its data to ransom, and use the device to infect other machines (known as a worm).
The patch corrects the software product's programming, and effectively removes the vulnerability, so the malware in unable to exploit, or work properly when it is installed on to the machine.
The scenario above is precisely what happened when the Wannacry Ransomware attack exploited a vulnerability in the Microsoft Operating System's Server Message Block V1 (SMB), and was named 'EternalBlue'.
I was directly involved in this attack and the subsequent impact it had on patient care, and the effort required to recover with minimal damage. This is why security patching is a subject close to my heart.
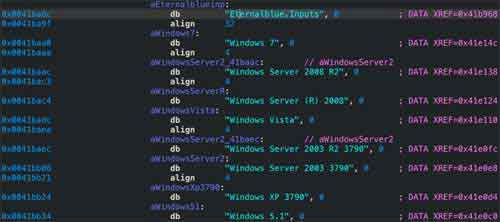 Software Application Security Patching Plan
Software Application Security Patching PlanEternalBlue Source Code Example
Source:- sentinelone.com
Occasionally, patches improve software products by enhancing or introducing new features.
It is also the case that some patching includes the replacement of the entire software product with a new version. The previous version is removed from your device and the new version is installed.
Patching is important to protect against new and evolving cybersecurity techniques.
Patches should be regularly applied to both the device's operating system, and any installed software applications.
This is because software vendors either know or are made aware of vulnerabilities in their products that are being exploited in the wild, which means cyber criminals are targeting such vulnerabilities with their malware programs.
Occasionally, software vendors will release an 'out of band' patch, often to address 'zero-day exploits', or those vulnerabilities that cannot be detected and prevented from running by antivirus products.
The consequences of a successful cyberattack can be catastrophic. Not only could they destroy or even sell your data, they could also subject you to identity theft and fraud.
The video below is a brief presentation that explains the fundamentals of system patching.
However, before you watch, it is worth noting that you need a patching plan to ensure you keep on top of all the different patching regimes used by the different operating system and applications providers. This is the focus of the next section.
The Fundamentals of System Patching Video
A Professional Patching Plan For Home Users
A software application security patching plan for the everyday home computer user must be robust, simple, and take up a minimal amount of your time when the plan is put in to action.
This is the holy grail for most professional businesses, and one that often eludes even the largest of organizations.
SingHealth, one of Singapore's major medical facilities, had 1.5 million patients personal details compromised in 2018 because they didn't apply a security patch to their e-mail clients that would have prevented the publicly available hacking tool from working.
Typically, distractions can mean security patches are not applied quickly enough, especially for newly disclosed vulnerabilities that are being actively exploited.
If they were not being exploited, they soon will be because details of the vulnerability are often released alongside the security patch to resolve the issue,
This is where the software application security patching plan comes in to effect. Consider the following 6 steps to develop your personal patching plan.
1. Identify All Household Devices
Often referred to as an inventory, the first step of your plan should be to account for all the devices in your home, including desktop computers, laptops, mobile phones, tablets, broadband routers and even Smart TV's.
2. Review All Software
Each device will have an operating system and applications installed, including games and other entertainment packages. For each device, note what is currently installed.
Discuss and agree which applications to remove, and then remove them using a product such as Revo Uninstaller.
If these applications are not being used, then it is likely they are not being patched. Removing unused software is a good idea to reduce the 'attack vector', or the means of being subject to a cyberattack.
Furthermore, consider standardizing on the software used in your home. For example, consider using the same version of Microsoft Office, or Cloud hosting solution, on all of your devices where appropriate. Fewer software products means less patching work.
3. Follow Vendor Patch Release Announcements
Common software and providers such as Microsoft, Apple, Adobe Reader and Google all publicize details of the latest patch releases for their products.
Understanding when this happens can give you an advantage for applying new patches early. For example, Microsoft releases the majority of their security patches on the first Tuesday of every month, which is also known as 'Patch Tuesday'.
This step can be quite time-consuming to set up. I think it is worth the effort; However, I understand not everyone has time to do this. Have a look at the next section for tools and approaches to automatically check for updates.
4. Review Known Issues With New Patches
Not all patches work perfectly first time. Often, vendors will recall new patches or even release updates to those patches when issues are reported. This can delay when new patches are applied, but occasionally, it is worth the short wait.
Ivanti is an excellent resource for details regarding patch releases and software product End of Life announcements. It can get a bit complicated to understand, but worth a look.
 Software Application Security Patching Plan
Software Application Security Patching PlanIvanti Patch Release Infographic
5. Test Test Test
If possible, test the new patches on a device that is used less frequently, or has less impact if an issue occurs. This way you know the patches work before applying to your main devices.
In the event you have a catastrophic failure because of a faulty patch release, make sure you have a good backup plan in place for all of your devices and data.
6. Regularly Review Device Patching status'
Some time, patching can get out of sync, especially if you have many devices to patch. A review every 3 months or so is all that is required.
In the next section, we have a look at options for making the patching process much easier to implement.
Tools You Can Use To Make Patching Easier
No one wants a complication and time-consuming software application security patching plan. This is where targeted automatic updates and specific software tools, if used correctly, can make all of our lives easier.
Below is an outline of my patching plan for a couple of my home device, namely a Laptop and an Apple iPhone.
Windows Laptop
Below are the screenshots for my Windows Update setup. Here I've specified my main timeframe I use my Laptop, so patches are not actively applied during this time and inadvertently disrupting my work with surprise reboots.
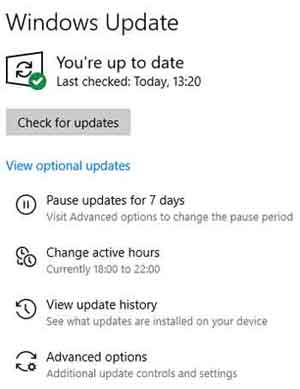 Software Application Security Patching Plan
Software Application Security Patching PlanMy Windows Operating System Update Set Up
In addition, I have the option to receive updates for other Microsoft products when updating the operating system. This way any supporting Microsoft software, such as Visual Studio, are also included in any update activity.
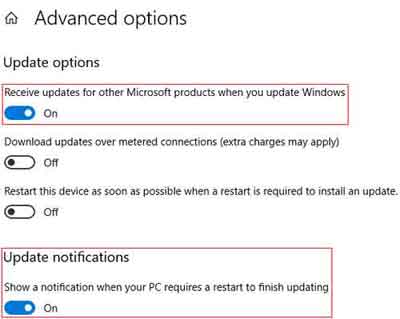 Software Application Security Patching Plan
Software Application Security Patching PlanMy Windows Operating System Advanced Options Set Up
Modern operating systems are fairly stable, so I have no issues with applying these patches quickly after release. So far. I have experienced no issues.
I tend to manually check for updates the days after patch Tuesday, and every Sunday thereafter, to catch any out of band releases.
Furthermore, I also use the default settings for the inbuilt Microsoft Defender Anti Virus solution. This product is excellent for home users, and it's free.
However, I also have the MalwareBytes (Premium) Anti Malware application installed, and setup for full overnight scans.
 Software Application Security Patching Plan
Software Application Security Patching PlanMalwarebytes Is More Than
An Anti Malware Product
For application patching, I use the free Patch My PC product. It is brilliant, and can be configured to automate your (consolidated) application updates silently, so there is minimal disruption, and frequently because application updates are likely to be issued on an almost daily basis across multiple application vendors.
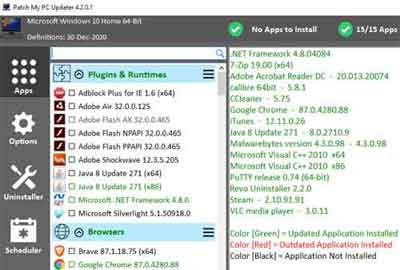 Software Application Security Patching Plan
Software Application Security Patching PlanPatch My PC
The video below is an excellent overview of Patch My PC, and touches on all the different configuration options, from recommended patching schedules, to specific technical set-ups such as creating a restore point before any application updates are undertaken.
Patch My PC Overview Video
I run this product once a week, manually, every Sunday. This is because I like to have some element of control about when application patches are applied to my main Laptop.
I have the recommended schedule set up on another device as a means of testing the updates before deploying across the other devices in the home.
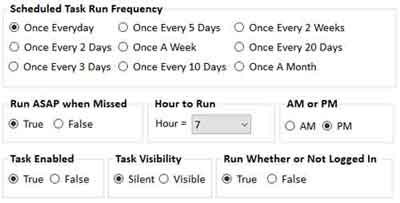 Software Application Security Patching Plan
Software Application Security Patching PlanPatch My Pc Suggested Schedule
Patch My PC covers over 300 applications. However, the product does not cover every single application. For example, it doesn't appear to cover Apple iTunes, so these apps will need to be included in your wider patching plan.
Apple iPhone
My approach for maintaining the iOS and Apps on the iPhone is simple. All I do is manually check and refresh the Software Update settings (for the iOS) and the App Store for all installed applications. I do this one a week.
 Software Application Security Patching Plan
Software Application Security Patching PlanApple iPhone App Updates
Software Application Security Patching Plan | Final Thoughts
Updating software is here to stay, and I think we all have to take a level of responsibility for protecting our devices. We cannot rely on software vendors alone to keep the risk to our data at a minimum.
The software application security patching plan outlined above is something you can either follow to the letter, or take the appropriate parts and apply to suit your needs.
It is worth having a brief look at professional articles on software patching, such as this one from White Source.
Having been part of the technology industry for over 20 years, I can identify with the issues organizations have kept their estates patched. I hope this article has been successful in bringing in some of the best practices from the IT world, in to your world.
Was this page helpful?
Thanks! ✅

