The Stuxnet Virus Attack | What Actually Happened
Stephen Harrison B.Sc. (Hons), M.Sc., MBCS, CITP
The Stuxnet virus attack in 2010 was a landmark cyber event that propelled the world in to an era of cyber warfare between nation-states.
This was a sophisticated attack on Iran's nuclear weapons programme using advanced malware techniques never seen before.
The ability of hackers to destroy hardware and put nation utilities service, such as their power facilities, on alert, was only seen in action and espionage movies, until now.
This article describes the Stuxnet virus attack and how it managed to damage the Natanz uranium enrichment plant in Iran without detection. This is even more remarkable when you consider the size of the worm was less than 500Kb, and had to be released via USB pens.
Keep up with the latest news and developments
Sign up to the eComputerZ Newsletter
The free A to Z of performing BIOS updates guide that anyone can follow.
✔ A checklist of important actions to perform throughout the update process.
✔ Further supporting information to aid your update plans.
✔ My unique approach for sourcing the latest BIOS versions for any motherboard manufacturer.
Sign up below for instant access to the guide, or by going to the Subscription page for more details.
I never share information with third parties and your details are secure.
I aim to issue newsletters at the start of each month.
Contents
What Is Stuxnet?
Stuxnet is a computer worm, which is a form of malware that can self-replicate to other computers on a network if certain conditions are met, such as the right software vulnerabilities that the worm can exploit.
Stuxnet was created with the sole aim of destroying specific, physical equipment, such as the centrifuges used in the Iranian nuclear facility to enrich uranium for use in nuclear weapons.
The centrifuges are usually controlled by computers called Supervisory Control and Data Acquisition Systems (SCADA) and Programmable Logic Controllers (PLC).
 Stuxnet Virus Attack
Stuxnet Virus AttackSatellite Image Of The Natanz Nuclear Facility In Iran
Source:- wired.com
The notoriety of this worm was confirm when it appears to have been created by nation-state intelligence agencies.
Although no one has claimed formal responsibility, it is highly suspected the culprits were the U.S. National Security Agency (NSA), the Central Intelligence Agency (CIA), and the Israeli Intelligence Agency.
Return to the Table of Contents
The Story Behind The Stuxnet Creators
The U.S. and Israeli Intelligence agencies collaborated on developing the worm in a classified program, code named Operation Olympic Games
This program is suspected of starting in 2005, under President George W. Bush, and continued under the Presidency of Barack Obama.
The Americans and Israelis were concerned about Iran's drive to develop their own nuclear weapons, and the consequences this would have on the stability of the middle-east, and the safety of Israel.
The Stuxnet program was likely triggered by the comments made by Iran's President Mahmoud Ahmadinejad about Israel being a "disgraceful bot" that should be "wiped off the face of the earth".
 Stuxnet Virus Attack
Stuxnet Virus AttackPresident Mahmoud Ahmadinejad's Visit To The Natanz Nuclear Facility
Source:- timesofisrael.com
Operation Olympic Games was therefore seen as a non-violent alternative to curtailing Iran's nuclear programme.
At the time, there was uncertainly about whether such as cyber attack on hardware was even possible.
However, according to Kaspersky's Roel Schouwenberg, it is rumoured that the results of a prototype Stuxnet which destroyed a test centrifuge was shown to the U.S. government in the White House Situation Room.
I was following these discussions that the go ahead for Operation Olympic Games was given.
It is estimated by Kaspersky security experts, some of whom were involved in the reverse engineering of the Stuxnet programming code, that it would have taken a team up to ten coders, two to three years to create this sophisticated worm.
Return to the Table of Contents
How Does Stuxnet Work?
The Stuxnet worm was carefully crafted to exploit 4x Microsoft Windows operating system zero-day vulnerabilities that were known to the intelligence agencies, but were not publicly disclosed.
The four exploited vulnerabilities were:-
- The LNK file extension for creating shortcuts;
- A shared print-spooler vulnerability;
- Two vulnerabilities related to privilege escalation.
The LNK file extension was used to enable the worm to spread using USB pens. The shared print spooler vulnerability was used to spread the worm on networks using shared printing facilities; a common sharing mechanism at the time.
The privilege escalation exploits enabled the worm to covertly execute its code and cause the centrifuge damage.
The process of infection was remarkable, yet simple in its execution across three main phases.
Phase 1 targeted the computers used to manage the SCADA and PLC devices that controlled the centrifuges.
The nuclear facilities network was not connected to the wider Internet (known as air-gapped).
Therefore, the worm's infiltration mechanism was by USB Pen. This was achieved by the intelligence agencies infiltrating five of the nuclear facilities suppliers and covertly adding the Stuxnet code to their systems.
Although the companies have never been formally identified, they are believed to include Fooland Technic, Bahpajooh, Neda and Control Gostar Jahed.
The engineers at these companies were cleared to work on the SCADA and PLC's, and anti-virus systems at the time could not have detected the malicious code.
Once the USB Pen's were plugged in to the nuclear facilities Windows-based computers, the Stuxnet worm replicated itself to all other available Microsoft Windows-based computers on the nuclear facilities networks.
Phase 2 of the code then identified the specific Siemens's Step 7 Software running on the facilities Microsoft-based computers.
The Siemens's Step 7 application was used to control the SCADA and PLC's, which in turn controlled the centrifuges.
Phase 3 of the code then execute the payload, which manipulated the controls that managed the speed and duration at which the centrifuges spun at, causing them to burn out.
Whilst the speed was being manipulated by the Stuxnet worm, it was relaying false data to the SCADA's and PLC's and therefore the Siemens Step 7 application, giving the impression that there was no issue to the instrument mechanics working at the facility.
In 2009, an earlier version of Stuxnet was manipulating the valves to increase the pressure inside centrifuges, damaging both the valve and the centrifuge, derailing the uranium enrichment process.
Below is an excellent depiction of how the Stuxnet virus attack was executed.
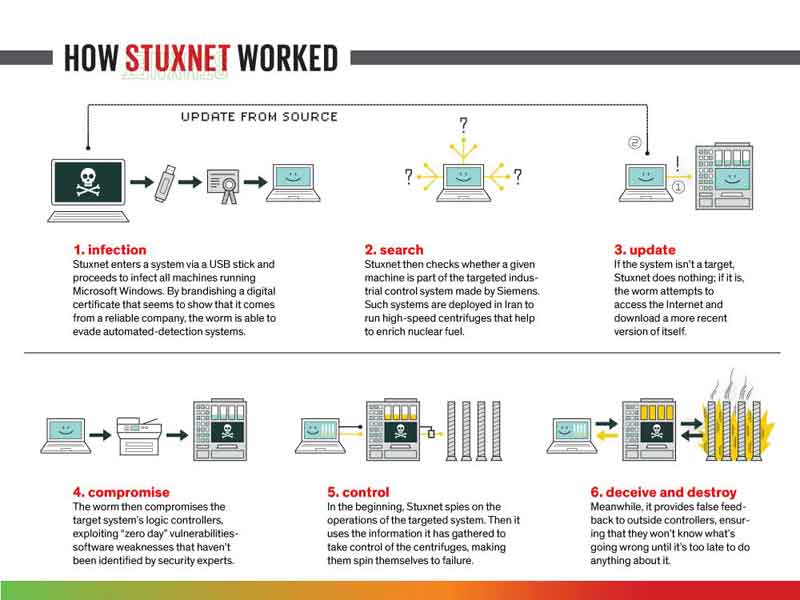 Stuxnet Virus Attack
Stuxnet Virus AttackPictorial Description Of How The Stuxnet Attack Worked
Source:- spectrum.ieee.org
The worm was covertly damaging Iran's nuclear weapons ambitions for at least a year before it was discovered in 2010.
The Iranian technicians, and even the inspectors from the International Atomic Energy Authority (IAEA) noticed the centrifuges failing at an alarming rate.
The cause was a complete mystery. Several hundred centrifuges out of around 6, 000 in total were damaged beyond repair by the initial Stuxnet attacks, and were subsequently replaced.
More damage was then caused by the updated Stuxnet worm, where nearly 1, 000 centrifuges were destroyed.
Return to the Table of Contents
The Discovery and Subsequent Events
The Stuxnet virus attack was eventually discovered in 2010, triggered by two separate incidents.
The worm had been released on to the wider Internet. Again, no one is claiming responsibility, but it is suspected this was done by the Israeli's.
Fortunately, because the worm targeted specific Siemens's software, no widespread damage was caused.
However, when computers were crashing and randomly rebooting in Iran, a security firm called in to investigate discovered the malicious code.
 Stuxnet Virus Attack
Stuxnet Virus AttackAn Example Of The Reverse Engineered Code That Enabled Stuxnet To Work
Source:- securelist.com
The second incident was triggered by a PLC engineer posting an unusual issue in a Siemens user forum.
All of their computers was having an identical problem, with an error message appearing in their Siemens Step 7 application.
When they rebuilt their problematic computers and used a CD or DVD to transfer application data from the problematic computer to a newly built computer, the error message disappeared.
However, when they used their USB Pens to transfer the application data, the error message re-appeared. Although a virus was suspected, it was never proven in the forum because antivirus programs were unaware of Stuxnet, and were unable to detect or remove the malicious code.
Return to the Table of Contents
The Stuxnet Virus Attack | Final Thoughts
The importance of the Stuxnet virus attack cannot be underestimated. It was a landmark event in geopolitical conflicts and set humanity on a course of increasingly sophisticated cyber attacks, such as the Wannacry attack in 2017.
What is to stop state-sponsored cyber attacks and other groups from using the now public Stuxnet code to create variants and attack other national facilities such as water treatment plants, gas lines and electricity plants?
It is alleged that Stuxnet was designed to expire in 2012. However, once the worm was discovered, Siemens issued security patches that prevented Stuxnet from working.
In total, the Stuxnet virus attack infected the SCADA and PLC controller software in at least 14 industrial sites across Iran, including the Natanz nuclear facility.
Take a look at this article from Wired entitled "An unprecedented look at Stuxnet, the world's first digital weapon" for an excellent review of the events in 2010.
Finally, watch the short video below that concisely describes the Stuxnet events.

