Spectre And Meltdown | What was That All About?
Stephen Harrison B.Sc. (Hons), M.Sc., MBCS, CITP
Spectre and Meltdown are essentially a collection of critical vulnerabilities found at the hardware level of almost all Central Processing Units produced since 1995! They were officially made public on the 3rd January 2018, by cyber security researchers in Google's project zero team. This was an effort to give computing providers a chance to patch their systems, before active exploitation by cyber criminals.
The Spectre and Meltdown vulnerabilities, therefore, present an albeit difficult opportunity for cyber criminals to execute carefully crafted malware, and effectively have access to everything on your device that is running at that time, whether that be a desktop computer, laptop, mobile device, or even cloud hosted services. This includes, for example, passwords, images, e-mails, social media messages and your personal documentation.
Almost all computers worldwide were affected, and the efforts in to fixing these vulnerabilities is difficult, considering any fixes can technically slow down the performance of your device.
In this article, we look at Spectre and Meltdown in more detail; what they are, and how they "work". We then look at the consequences of these vulnerabilities in more detail, and cover the more common questions asked about each vulnerability type.
Keep up with the latest news and developments
Sign up to the eComputerZ Newsletter
The free A to Z of performing BIOS updates guide that anyone can follow.
✔ A checklist of important actions to perform throughout the update process.
✔ Further supporting information to aid your update plans.
✔ My unique approach for sourcing the latest BIOS versions for any motherboard manufacturer.
Sign up below for instant access to the guide, or by going to the Subscription page for more details.
I never share information with third parties and your details are secure.
I aim to issue newsletters at the start of each month.
Contents
What Is Meltdown?
When you are using your computer, the operating system and your applications use different areas of your system's memory that are isolated from each other. This is essential to the smooth running of your device.
However, Meltdown intentionally breaks this memory isolation, but between your applications and the operating system. Attackers can then access your computers memory, and therefore access all the sensitive information across your applications and operating system.
It does this through your Central Processing Unit's Meltdown vulnerability. To understand how Meltdown works, you need to understand how processors work, which can be a little tricky to explain. However, I have attempted to simplify the description below, and the illustration captures the narrative quite nicely.
So, your CPU processes, or executes, instructions all the time. For example, when you load your web browser, save a document or write an e-mail. Logically, these instructions require permission, often from the operating system, before they are processed from their allocated memory space, by the CPU, i.e. your web browser loads, e-mails sends, or document saves.
However, if permission is refused by the operating system, you receive an error message, which is similar to the "Program critical error" or a "Memory could not be read" message, that occurs when the memory space holding the data for one program, has been overwritten or corrupted by another, causing us to lose work, i.e. your web browser crashes, e-mail fails to send, or your document fails to save.
Fortunately, this seldom happens, ad when it does, it is generally due to a data processing error, or other computer issue.
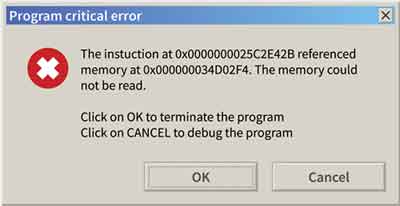 A Typical Program Critical Error
A Typical Program Critical ErrorSource:- howtogeek.com
However, to improve computing speed, it became common practice, over 25 years ago, for instructions to be speculatively executed, i.e. the CPU processes the instructions from memory, then asks for retrospective permission from the operating system whether this was OK to do or not.
This approach allows for common or routine tasks that occur frequently could be "anticipated" and executed before they were requested, ensuring computers performed efficiently.
If the speculative processing of instructions from memory is OKed by the operating system, then your computer performs quickly and efficiently. However, if the operating system does not give permission for the instructions to be processed, the expected outcome is rejected, and the program critical error, or equivalent, appears on your screen.
It is this speculating time that enables the Meltdown vulnerability to be exploited.
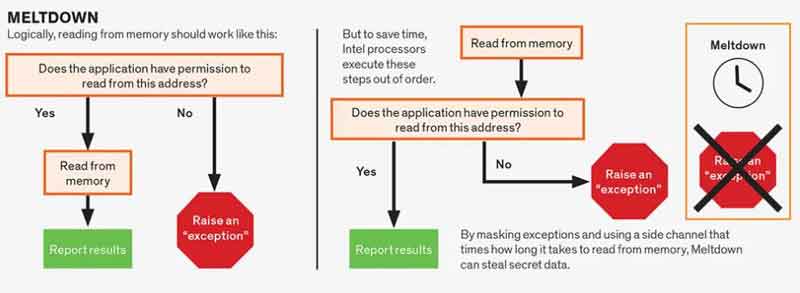 Spectre and Meltdown
Spectre and MeltdownHow Meltdown Works
Source:- spectrum.ieee.org
As outlined in the illustration above, the Meltdown vulnerability could be exploited by Malware through a side channel into the CPU, that enables the stealing of sensitive data by masking the program critical error, and tricking the CPU into sending the data from memory to the hackers.
Fortunately, there were software patches to address the Meltdown problem, so long as they are actually applied!
There is an excellent academic paper that explains Meltdown in excellent detail, but be warned, it is highly technical in nature.
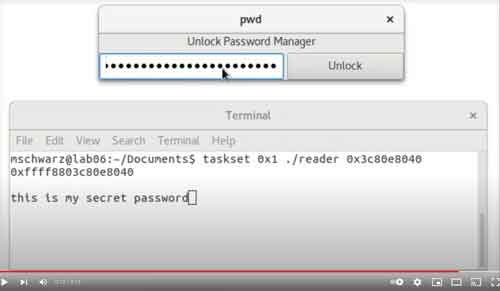
Finally, the video below shows how the Meltdown vulnerability could be exploited to steal your sensitive information. I found it fascinating.
Spectre and Meltdown
Meltdown Exploitation In Action Video
Return to the Table of Contents
What Is Spectre?
Spectre is similar to Meltdown, in that the memory isolation for different instruction sets is broken. However, the key difference is that Spectre intentionally breaks the isolation between different applications, whereas Meltdown does this between applications and the operating system.
The process for exploitation is basically the same as Meltdown, where speculative execution of instruction sets from memory are exploited through a side channel.
However, Spectre is more difficult to exploit than Meltdown, and is therefore more difficult to mitigate. There are many applications available today, and this is why application to application-based exploitation is more difficult to completely address.
Spectre will be around for years to come. It has not been fully addressed at the time of writing, although there are some mitigations through software patches.
There is also an excellent academic paper that explains Spectre in excellent detail, but be warned, it is highly technical in nature.
Return to the Table of Contents
What Did All This Mean?
At the time of writing, Spectre and Meltdown hasn't had a huge, noticeable effect on computing performance. However, before some patches were released, it was expected that computer devices would perform more poorly because the speculative execution afforded to CPU's would have to be scaled back or cancelled.
Confidence was knocked in the technology industry. Time and time again, news of malware attacks and major software flaws, such as the Apache Log4j vulnerability (December 2021) meant that we as a society did not trust technology to keep our details safe. By the end of the 2010s, Social Media was powerful in influencing opinion.
However, as is often the case with these things, they are forgotten about as time passes, or until the next major cyber event takes place.
Spectre and Meltdown re-iterates the need to have a robust software patching plan in place. This typically gets overlooked, but should be taken seriously. For the various flavours of Spectre, and Meltdown in particular, the fix was to separate the execution instruction from the actual data, keeping the data secret, e.g. your passwords. However, this also meant extra work for your computer to do, which could sow things down somewhat.
Anti Virus programs are unlikely to detect Spectre and Meltdown because they are part of your computer's intended workings. However, a good antivirus program should be able to detect the malware program being used to exploit the vulnerabilities.
To check if your device has the Spectre and Meltdown vulnerability, take a look at the Spectre Meltdown CPU Checker Tool from Ashampoo. It is free at the time of writing. I used it on my device and were my results.
 Spectre and Meltdown
Spectre and MeltdownCPU Checker Results
Return to the Table of Contents
Spectre And Meltdown | Final Thoughts
It is worth noting that although application and operating system software patches help to reduce the risk or even mitigate Spectre and Meltdown, there are some patches produced by vendors that also need applied. This ensures full protection. Therefore, firmware or BIOS updates are also required.
To ensure future products are not subject to Spectre and Meltdown, Intel, AMD and others were looking at complete CPU redesign, so the speculative element of CPUs is retained, but without compromising performance or security. Suppliers often do this, as we have seen several times with Microsoft, e.g. Internet Explorer's replacement by Microsoft Edge.
The fortunate thing is Spectre and Meltdown have been in existence since 1995, and to date, have not been actively exploited to anyone's knowledge. To do so is difficult, and I expect, costly in time and money for the cyber criminal. Why go to all that expense, when there are easier vulnerabilities to exploit?
Finally. I leave you with the link to the National Cyber Secure Centre's Spectre and Meltdown guidance, which so worth a read, and the IEEE's guide to how Spectre and Meltdown actually works.
Also, watch the 3-minute video below. It is an excellent explanation of what Spectre and Meltdown is.