The Edward Snowden Leaks | What Happened and the Ramifications
The Edward Snowden leaks caused quite a stir in June 2013, when he leaked an estimated 1.5 million classified files on U.S. Intelligence service top secret cyber activity.
Along with whistleblowers such as Julian Assange and Chelsea manning before him, Ed Snowden's expose really put the spotlight on the extent of government mass surveillance, and its consequences, both good and bad.
In this article, we look at who Ed Snowden is, what he did, and the nature of the leaks that caused so many a lot of concern.
We also look at how the Intelligence Agencies could get their hands on such large volumes of personal information, and the ramifications that we are still experiencing today.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the Ultimate BIOS Update Pack
- Includes a set of checklists, flowcharts, and your Beep Code Finder support your BIOS update process
- Also includes a full set of eBooks including a Survival Guide and step-by-step Support Guide
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.

Who Is Ed Snowden?
Ed Snowden is a computer intelligence consultant, and worked for a management and Information Technology firm called Booz Allen Hamilton Holding Corporation. His working carer is distinguished, with previous roles in the Central Intelligence Agency (CIA) as a top cybersecurity expert.
Booz Allen Hamilton was a subcontractor for the National Security Agency (NSA), and Snowden was based in the NSA's Hawaii Regional Operations Centre.
His work was mainly focused on monitoring activity by China and North Korea, and developing new ways to hack into secure Internet communications and telephone systems.
He was based in Hawaii, working for the NSA, through Dell, initially, then later with Booz Allen Hamilton, for around 15 months before 'he was let go' in June 2013.
Snowden describes himself a “just another guy”, but he is anything but that. With an IQ test score of over 145, and a family background in law and public service, it appears he had a solid foundation on which to build a successful life.
From what I have read, it appears Ed Snowden is a principled guy who became disillusioned with the culture of how intelligence services operated, and the types of activities they were undertaking. This led to him leaking lots of sensitive material in a whistleblowing fashion, much to the dismay and anger of the U.S. Government.
In the video below, Snowden explains his rationale for whistleblowing, and the problems he has with how the U.S. Government acquired its intelligence on its citizens (and others) and why he thinks this motivation fundamentally undermines democracy.
The Edward Snowden Leaks | The Interview
What Did Ed Snowden Do?
Ed Snowden's notoriety, or hero status, come from his intentional leaking of highly classified NSA information whilst working as a subcontractor for the CIA.
In June 2013, he disclosed that fact that the NSA was collecting the telephone records of millions of American's who were with Verizon daily, without their knowledge.
I expect the NSA's rationale is to analyse the data and search for patterns in behaviour that could indicate a potential threat to national security. After all, no one wants to experience another 911. If you tell people this is what you are doing, the 'bad guys' will simply find another way to communicate.
Snowden also disclosed the fact that that NSA tapped into the servers of nine Internet companies, including Google, Facebook and Microsoft, in a mass surveillance program code-named Prism.
The program cost $20m a year to run, and effectively captured information such as e-mails, videos, video calls, images, Social Media data and login details of all users of these services, such as Google Mail.
The image below if from a leaked NSA Presentation in April 2013, which described the Prism program and its intentions.
 Edward Snowden Leaks
Edward Snowden LeaksPRISM Case Document Page
There is an excellent Q&A article about the Prism program, including the NSA's response regarding the data collected and specified targeting of information analysis that they say did not include U.S. citizens.
In all, the Edward Snowden leaks released over 7, 000 documents between 2013 and 2014. A timeline of leaks is detailed here, but the highlights include:-
- An 18-page memo showing Barack Obama ordering intelligence officials to put a list together of overseas cyberattack targets, with 231 taking place in 2011;
- The UK Government Communications Headquarters (GCHQ) tapping the telephone and internet communications of politicians attending G-20 meetings in London;
- The NSA provision of covert surveillance information to U.S. Diplomats to improve their negotiation advantage at the U.N Summit of the Americas;
- The U.S. Intelligence “Black Budget” was an estimated $52.6 billion back in 2013;
- The NSA's unfettered access to everyone's mobile phone data.
The list is extensive, and includes both UK and U.S. governments. Some actions are widely applauded by some, including strategic missions to combat terrorism and nuclear activity, to those that are greeted with horror, such as collecting your personal data.
How Did the Intelligence Agencies Conduct Their Surveillance Activities?
With budgets running in to billions of dollars, it will come as no surprise that intelligence agencies have many tools and services at their disposals. However, one such tool revealed by Snowden is called XKeyscore.
This program, according to the Edward Snowden leaks, enables NSA analysts to access and search different databases of personal information, such as your Internet browsing history and online chats, including in real-time.
“I, sitting at my desk, could wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email”.
— Ed Snowden
The information gathered was copied to a central database, and the analysts could run various search routines to discover patterns in behaviour, and keyword searches to help determine if further investigations were required.
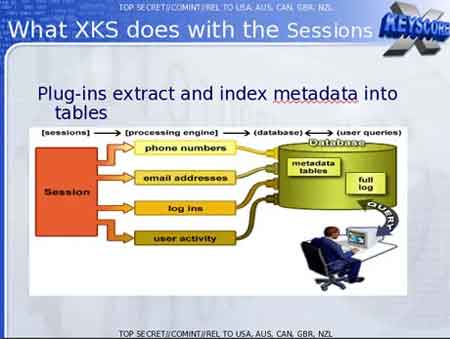 Edward Snowden Leaks
Edward Snowden LeaksHow The NSA Captured Personal Data For Analysis
This claim was refuted by the U.S. Government. However, the leaked presentation on XKeyscore seems to back up what Snowden is claiming.
Basically, the NSA analysts completed a basic form with their justification for access, which was usually immediately granted. In addition, NSA documents claimed that by 2008, over 300 terrorists has been captured using intelligence gathered by XKeyscore.
In addition, the NSA used a tool called DNI Presenter to read e-mail content, and enabled XKeyscore to read the content of Facebook and Messenger chats.
The image below shows the technical steps they effectively bypass the authentication we use of a daily basis to access our online accosts.
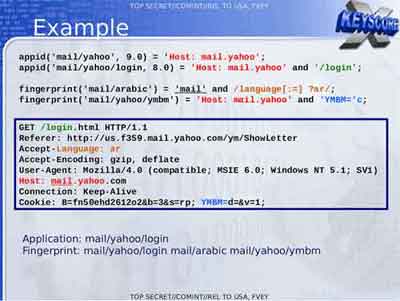 Edward Snowden Leaks
Edward Snowden LeaksScreenshot of An NSA Presentation About Accessing Personal E-Mail Accounts
The scale of surveillance activity should not be underestimated. Even back in 2007u it is claimed through the Edward Snowden leaks that up to 2 billion records were added to the NSA databases each day!
This volume of data can run in to terabytes of storage required. This is expensive to run and support, and in my experience, a nightmare to back up and ensure the system continues to perform efficiently.
The documents revealed that the NSA can only keep the actual data, such as e-mail content, for up to 5 days, whilst storing the metadata, i.e. such as your IP address, telephone number etc., for up to 30 days. The NSA keep data of interest for much longer.
What Were The Ramifications?
The consequences for Edward Snowden, and his family, were huge. On June 14th 2013, he was charged with three felonies, theft of government property (the leaked documents) and two counts of violating the 1917 Espionage Act. This is a total of 30 years in jail.
However, by this time Snowden had managed to secure temporary residency is Russia, who refused to extradite him to the U.S. to face his charges. In addition, Snowden claims he cannot receive a fair trail.
The U.S. Attorney General at the time, Eric Holder, had written to the Russian Minister of Justice, Alexsander Konovalov, in an attempt to have Snowden sent back to the U.S. for trail. The letter makes interesting reading.
By the end of the 2010s, Snowden had a settled life in Russia, and is now a permanent Russian citizen.
The U.S. Government, on the other hand, is refuting many of Snowden's claims, and is making the case for national secret activity to keep its citizens safe.
In a statement to the Guardian, the NSA said: “NSA's activities are focused and specifically deployed against – and only against – legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interests.”
In addition, such disclose of sensitive information, such as the Edward Snowden leaks, puts field operators at risk of exposure, and reduces the ability to prevent bad things from happening.
The Edward Snowden Leaks | Final Thoughts
The Ed Snowden leaks put the spotlight on the rapidly evolving use of online technology and how it can be used for both good and bad.
The subsequent debate around online privacy and covert surveillance will not be concluded anytime, soon. There are merits in both sides of the argument, but it is a complex, interwoven set of subjects, that is unlikely to declare a clear “winner”.
In subsequent years we saw other leaks of sensitive information, including the Panama Papers in 2016, exposing the financial records of well-known and wealthy people who have offshore holdings for tax purposes and other reasons.
In many ways, the internet is a permanent, auditable record of our activity, and for good or for bad, it can often be retrieved and used for many reasons
As our online activity evolves, I suspect we will see more leaks, and more efforts to secure our date. The Edward Snowden leaks are a major factor.
